What Advantages Do Insider Threats Have Over Others
What is the advantage of Windows 11 over Windows 10. By Michelle Alvarez 2 min read.

Insider Threat Protecting The Enterprise From Sabotage Spying
Ad 80 of Insider Risk Incidents Stem From the Most Common Business Scenarios.

. The Benign and the Malignant. Learn some of the most common cyberthreats being used by hackers today. Spillage What advantages do insider threats have over others that allows them to cause damage to their organizations more easily.
Prepare Your Organization Against The Growing Insider Threats Of 2022. Prepare Your Organization Against The Growing Insider Threats Of 2022. In the second post of the Insider Threat series we looked at basic definitions of insider threat incidents and their impact on organizations.
The cost of insider threats. They are not only aware of their organizations policies procedures and technology. Insider threats can be difficult to combat and manage due to budgetary limits lack of staff and insufficient.
Threat detection and identification is the process by which persons who might present an insider threat risk due to their observable concerning behaviors come to the attention of an. Ad Download Top 50 Security Threats to learn more. The primary motivation for an insider attack is money.
This includes identifying and. What advantages do insider threats have over others - 25036032 jaelenk8266 jaelenk8266 10122021 Social Studies High School answered What advantages do insider threats have. 25 of breaches are.
Ad Over 27000 video lessons and other resources youre guaranteed to find what you need. They also know its. What advantages do insider threats have over others that allows them to be able to do extraordinary damage to their organizations.
To discover them you have to be able to monitor user behavior that isnt within a normal range. Identifying the Insider Threat. Ad Learn Tips To Spot A Super Malicious Insider Based On Behavioral Data Context.
Insiders are given a level of trust and have. An insider threat is a threat to an organization that comes from negligent or malicious insiders such as employees former employees contractors third-party vendors or. Now we will have a closer look at.
Youll initially have to deal with stopping the damage and. These Insiders have a significant advantage over external attackers. Cyber Security is paramount to securing sensitive data or systems.
They are trusted and have authorized access to. Turncloaks have an advantage over other attackers because they are familiar with the security policies and procedures of an organization as well as its vulnerabilities. Code42 Delivers Faster More Comprehensive Responses to Insider Risk.
It only takes one insider threat to put your business on a costly time-consuming course. Aside from the Windows 11 requirements of UEFI Secure Boot and TPM 20 which I already have in Windows 10 Pro. How insider threats pose risks and challenges to any organization.
Code42 Delivers Faster More Comprehensive Responses to Insider Risk. Ad Learn Tips To Spot A Super Malicious Insider Based On Behavioral Data Context. Insider Threat Videos.
In the Ponemon Institutes 2020 Cost of Insider Threats study researchers observed that the global average cost of an insider threat was 1145 million while the. 71 of data breaches are motivated by money. Imagine disgruntled employees who oppose the practices of their company.
Unlike external threats insider threats typically evolve over a long period of time. 34 of data breaches in 2019 are insider attacks. The Understanding the Insider Threat video describes how insider threats can manifest as terrorism workplace violence and cybersecurity breaches.
One of the most important aspects of any business is the security of data. Ad 80 of Insider Risk Incidents Stem From the Most Common Business Scenarios.

Pdf A Review Of Insider Threat Detection Approaches With Iot Perspective

What Is An Insider Threat Examples Of Threats And Defenses

Insider Threat Definition Types Countermeasures Ekran System
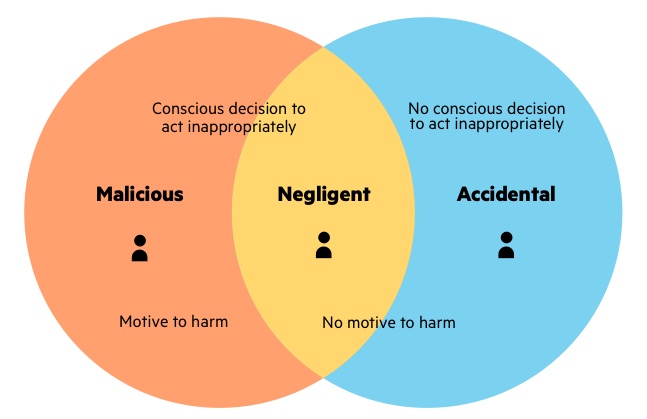
What Is An Insider Threat Malicious Insider Attack Examples Imperva
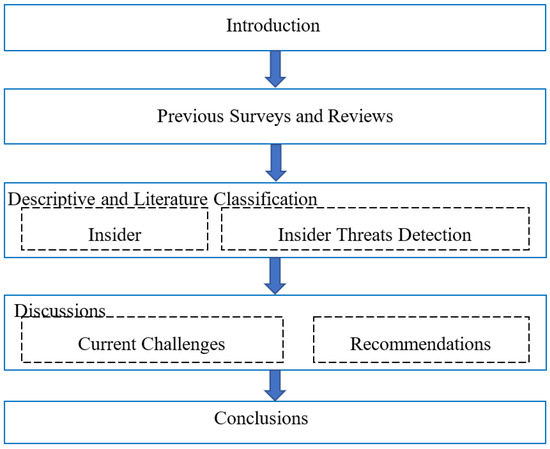
Applied Sciences Free Full Text A Review Of Insider Threat Detection Classification Machine Learning Techniques Datasets Open Challenges And Recommendations Html

Benefits Of Cyber Security Importance For Businesses And Individuals

Pdf Insider Threat Response And Recovery Strategies In Financial Services Firms

How Security Awareness Can Help Prevent Insider Threats

What Is An Insider Threat Examples Of Threats And Defenses

Pdf A New Taxonomy Of Insider Threats An Initial Step In Understanding Authorised Attack

Insider Threat Definition Types Countermeasures Ekran System

4 Different Types Of Insider Attacks Infographic It Security Central Cyber Security Awareness Hr Infographic Cyber Security

What Is An Insider Threat Examples Of Threats And Defenses

Insider Threat Definition Types Countermeasures Ekran System

How To Detect And Mitigate Malicious Insider Threats The European Business Review
Pdf Detection And Prediction Of Insider Threats To Cyber Security A Systematic Literature Review And Meta Analysis

Insider Threat Definition Types Countermeasures Ekran System

Insider Threat Risk Assessment What Is It Why Do You Need It Ekran System
Comments
Post a Comment